Not a virus. Not even a malware. Neither is the runner up… It’s the method of how malware is populated.
According to a report, the most common malware attack in 2007 is the notorious IFRAME.
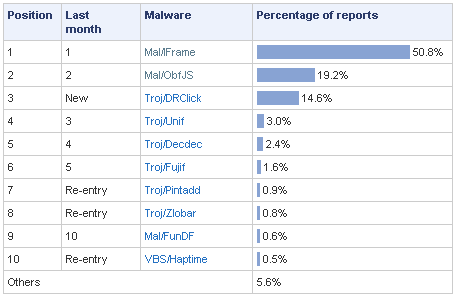
On our monthly and quarterly reports we provided more in-depth analysis of such top-ranking IFRAME and obfuscated code.
In Finjan’s terminology, the top-ranked virus IFRAME is not a malware or a virus, it’s more like how criminals are directing users’ browsers to a malware. Interestingly enough – the runner-up is “Mal/ObfJS†– Obfuscated javascript, again no a virus or malware but a simple technique to hide exploits from signature matching inspection.
How come? Well, remember that signature-based solutions are in a dire need to be able to stop the more common techniques employed by attackers (we have actually started to report on them during 2006), since the detection technology is limited in detecting the obfuscation and evasive techniques – typically signaturing the de-obfuscating portions of the script.
This has led to the recent reports of false-positives by multiple AV vendors lately, as active-content is becoming more and more complicated, and the ways to express an action in interpreted code are very complex – meaning that signatures in this realm are almost obsolete (you can see the honorary mention of the “DF†function (Mal/FunDF) in the 10th place, which is a signature on a specific de-obfuscating function – again, no mention of any malicious action taken by it, it’s just that it had it’s 15 minutes of fame when it was used by toolkits to deliver actual malicious code…)
Looking forward to 2008 I really hope that the industry as a whole will not be lagging behind the attack vectors as it did in 2007, and new and improved engines would enable end-users (especially consumers who do not benefit from the more sophisticated solutions offered to enterprises) to have better protection when using the internet.
I know what my new-year resolutions are – do you?
Leave a Reply